Introduction#
Create your Kube scanning test, for your custom plugin in against running kubernetes cluster. Here we are using the Kube-bench tool that checks the Kubernetes cluster is deployed securely by running the necessary checks documented in the CIS Kubernetes Benchmark.
Build gradle configuration for kube scanner#
deployIntegrationServer { kubeScanner { awsRegion = 'eu-west-1' logOutput = true kubeBenchTagVersion = "v0.6.5" command = ["-v", "3", "logtostrerr"] } }| Name | Type | Default Value | Description |
|---|---|---|---|
| awsRegion | Optional | By default it will read from config [~/.aws/config] file. | |
| logOutput | Optional | false | To Log the command and output executed while running the test. |
| kubeBenchTagVersion | Optional | latest | By default it will use the latest main branch. |
| command | Optional | ["kube-bench", "run", "--targets", "node","--benchmark", "eks-1.0"] | List of command for running the test. |
Under the hood#
Great, we now have the setup done. Let's figure out how it works.
How to scan the kubernetes cluster which is running on AWS (EKS)?#
- By Running the below command, we can scan the Kubernetes cluster which is configured as current-context in ~/.kube/config.
./gradlew clean kubeScanning- Firstly, it will clone the kube-bench repo with a tag to build/kube-scanning/kube-bench folder. As in the below illustration:
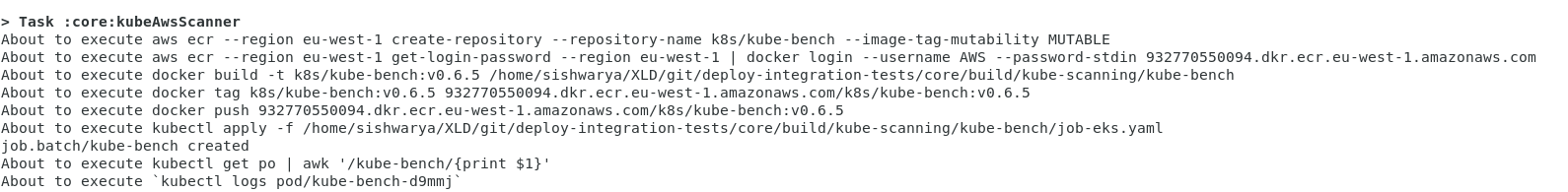
- Next, execute the steps for AWS-EKS-Cluster
- Create the repository in AWS ECR
- Take docker build of kube-bench with tag
- Push the created image to AWS ECR
- Update the job-eks.yaml with the latest image which we generate in a previous step and run the job.
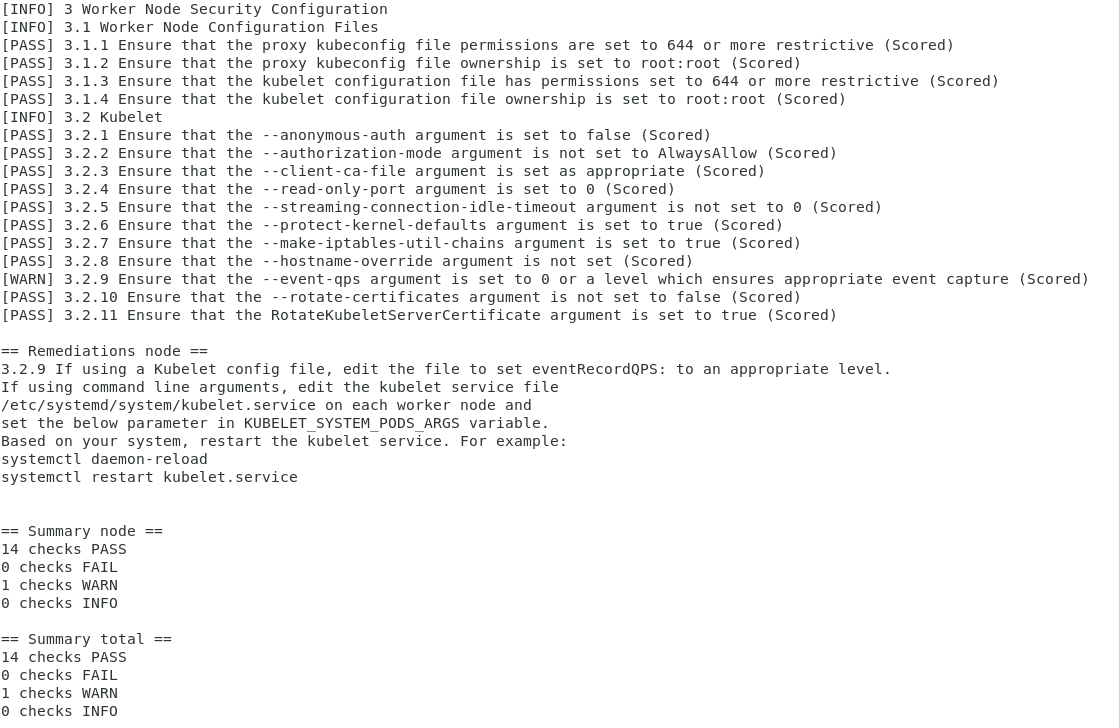
Once the above command execution is completed, we can find the report in build/kube-scanning/report folder, like the below sample log.
info
